DISCLOSURE: This post may contain affiliate links, meaning when you click the links and make a purchase, we receive a commission.
A firewall is an extremely quintessential part of any system. Accessing the internet without one is usually asking for trouble. You might have been annoyed by the many windows defender notifications about firewall permissions, but it plays a central role in keeping your system safe from malicious attacks through your network.
However, if you are using Linux, you might not have the fancy windows firewall but there still is a firewall service running in your system. If you are curious to read more about how it works and why there are two tools to interface with it, then keep on reading to learn more about it.
What Is A Firewall?
Before moving on to firewalld or iptables let’s take a look at what exactly a firewall does. A firewall is a set of rules that incoming or outgoing internet traffic have to follow.
When a data packet moves into or out of a protected network space, its contents (in particular, information about its origin, target, and the protocol it plans to use) are tested against the firewall rules to see if it should be allowed through.
Now in Linux, a user (particularly a superuser) can modify these firewall rules manually to add or delete certain check conditions. To do so, there are two (well, more than two, but for the sake of this article, let’s assume there are only two) tools that can be used, namely firewalld and iptables.
This may sound confusing as to why there are two tools in existence that practically do the same thing. However, there is a good reason for this, and it lies in the differences between these two tools. Read on below to find out what these are.
Iptables vs Firewalld
Difference Between Iptables And Firewalld
Firewalld is a more recent release compared to iptables. As such, it aims to provide a more streamlined user experience, all while utilizing the same tool under the hood. However, with the simplification, users lose some of the finer control that comes with using raw iptables. We take a deeper dive into their differences below:
Interface Level
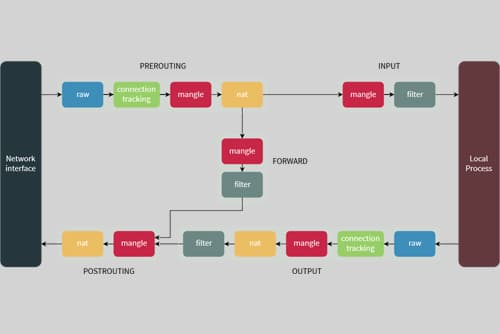
At the base of it, all lies Netfilter, which controls access to and from the network stack at the Linux kernel module level. Managing the firewall is done through this as well. Now for the longest time, the command line tool to interface with Netfilter was the iptables ruleset.
As such, it is a low-level implementation that interfaces directly with the Linux network stack. With iptables having an old and often inaccessible syntax, the need for a modern command line tool was felt. Thus, multiple higher-level Netfilter interpreters were born, one of which was the firewalld implementation.
That means that it offers users a prettier front end to manage firewalls, but under the hood, it still runs iptable commands, but that part is abstracted. Firewalld also offers the option for a GUI (Graphical User Interface) other than the command line interface. This is a huge plus if you only need to use it for simple personal needs.
User Type
With the prettier interface that a higher level Netfilter interface such as firewalld offers, it also takes away some of the raw power that comes with using iptables. With that said, due to its straightforward nature, firewalld is more suited for consumer-based machines or solo end users.
On the other hand, there are servers and complex multi-connected arrays of machines in local area networks. For building full-sized network solutions for such cases, the control and power that comes with iptables are necessary. A more straightforward user interface is put aside for low-level control.
A perfect analogy would be the debate between the C language and python in the programming space. For programming machines and low-level hardware, C is used, which has a more difficult syntax but offers low-level hardware control. While easier to use, Python is a higher-level language used for academia and machine learning implementations.
Protocol Support
Iptables does not support IPv6. To construct rules for this, you would need to use ip6tables, which is an entirely different tool. However, firewalld supports both IPv4 and IPv6 natively, so you can use a single tool to manage firewalls for both network protocols.
Run-Time Implementation
Iptables is a static tool that requires a firewall restart every time you make changes through it. This is a significant disadvantage as it slows down implementation and might be a cause of problems if you are working on a network device that is interconnected to a system of interdependent devices.
However, the firewall daemon manages the firewall dynamically and applies changes without restarting the whole firewall. Therefore, there is no need to reload all firewall kernel modules. This is what the firewalld tool takes advantage of. It manages the firewall dynamically, applying changes at run time without any stoppage.
Verdict
For basic actions such as removing a site from the firewall, the simplicity of Firewalld is hard to beat. Average users who don’t utilize advanced functionality are better suited to stick with it.
On the flip side, system admins and tech experts who like to have full control would require the power and accessibility that comes with Iptables. Here is a handy table that summarizes all we have discussed:
| Features | Iptables | Firewalld |
|---|---|---|
| Interface Level | Low level. Interacts directly with Netfilter | High level. Translated over to iptables on run time |
| User Type | Power Users. IT admins and server managers | End users without much need for advanced control |
| Protocol Support | Supports Ipv4 and not Ipv6 | Supports both IPv4 and IPv6 |
| Run-time Implementation | Static. Requires firewall restart to apply changes | Dynamic. Applies changes without firewall restart |
Conclusion
In the end, the choice between iptables or firewalld comes down to your use case. If you just need to add a few exceptions to your personal computer’s firewall, then getting iptables would be overkill. However, if you are setting up a network of kiosks in your shop, then iptables might be required.